Disaster Recovery
Protect your data with a disaster recovery process
Whether you prefer on-premise or cloud backup, we tailor a solution to match your business requirements.
With years of experience, we’ve crafted and maintained backup and IT disaster recovery solutions. Collaborating with various vendors, we offer multiple protection levels to suit your needs.
Many customers have invoked our disaster recovery processes which have enabled them to continue with business with minimal disruption. Our products facilitate failure simulation, enabling regular testing of disaster recovery plans for our customers.

Comprehensive disaster recovery strategies: Ensuring business resilience
Risk assessment and mitigation:
Identifying threats and vulnerabilities to your data and IT infrastructure, then implementing strategies to minimise their impact. By proactively addressing risks, businesses can safeguard their assets and maintain operational continuity.
Business Impact Assesses (BIA):
Assesses the consequences of disruption to prioritise recovery efforts and resources allocation. It also aids in developing resilience strategies such as business continuity plans to minimise downtime and ensure timely restoration of essential services.
Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO):
Establish realistic goals for recovery efforts, aligning with business needs. These objectives guide the development of disaster recovery plans, ensuring business continuity.
Data encryption and security measures:
Protect sensitive data during transit and storage through encryption protocols and security measures.
Documentation and communication plans:
Develop clear disaster recovery procedures, responsibilities, and communication channels to swift response.
Continuous monitoring and updates:
Regularly review and update recovery plans to reflect changes in operations and technology.
Employee training and awareness:
Educate staff on their roles and responsibilities during disaster to enhance resilience.
Regulatory compliance:
Adhere to industry regulations for data protection and disaster recovery to maintain trust and avoid penalties.
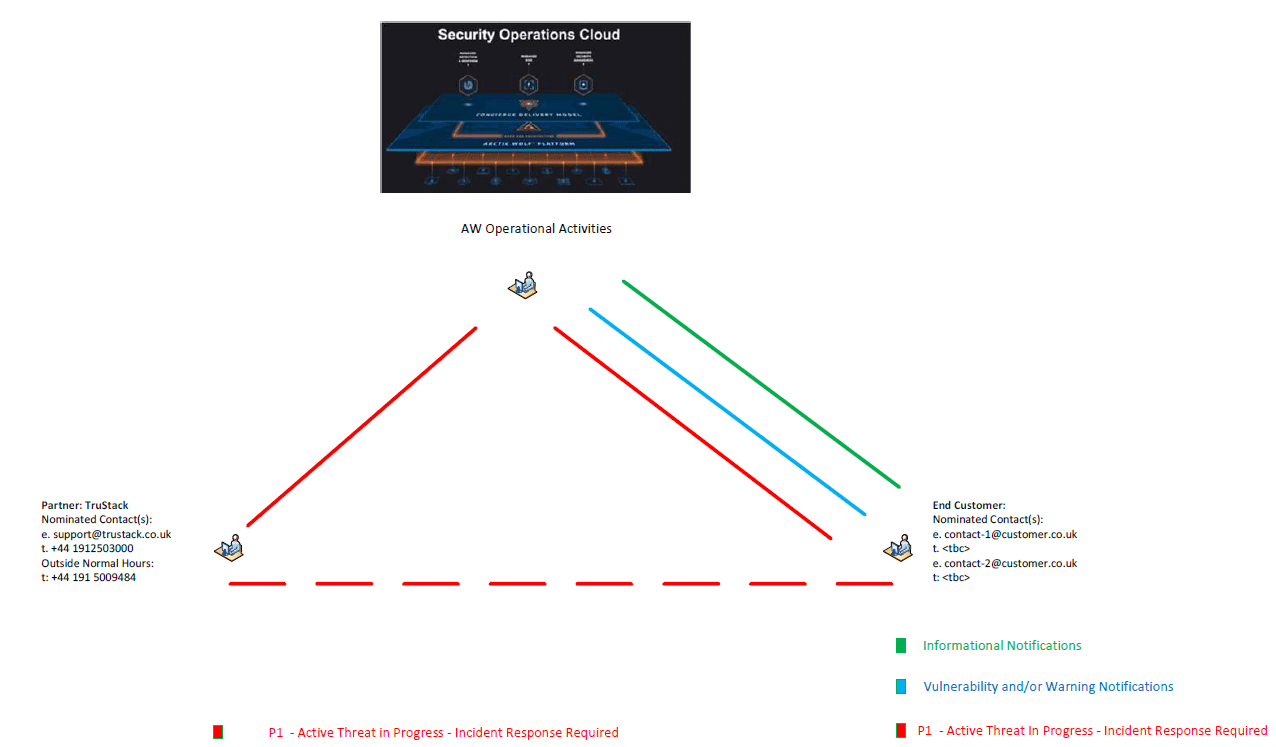
The retainer allows our clients to call us for help, containing and remediating any platforms supported by Trustack.
We aim to respond to all incidents within 1 hour, 24/7/365 (assuming you have out-of-hours support). During the ‘On-Boarding Process’ for each customer, we will define the process.
Arctic Wolf will inform Trustack of any P1 incidents classified as ‘Active Threat in Progress’. We will also inform you, the client, of any P1 incidents.
The following diagram outlines the process flow details.
Contact us to protect your data
A stack of services to keep you at the forefront of technology.
Relationships built on trust, honesty and integrity.
Unipres

Andrew Furness
Controller - Information Systems, Unipres UK Limited
“Trustack has been a trusted partner of Unipres for 11 years now. The stack of products they’ve worked with us to implement at Unipres has grown from an initial implementation of VMware vSphere to VMware Horizon, Veaam Backup and Replication and Trend Deep Security to name a few. We feel confident that they will implement IT solutions tailored to our business needs and deliver them to the requirements and quality Unipres expect as an organisation.”
Collingwood Business Solutions

Michael Ward
IT Director, Collingwood Business Solutions Limited
“Trustack are a trusted partner who have worked with us for a number of years. They know our business and have in depth knowledge of our complex infrastructure whether that be security, networking, virtualisation or any other parts that play an integral role in our success as an IT service provider and Insurance distribution business. Trustack have been a major part of Collingwood’s success working with us to enable us to scale accordingly with innovative solutions and robust security”
Muckle LLP

Andrew Black
Director of IT, Muckle LLP
“We rely on Trustack to help us deliver innovative, cost-effective technology. Their extensive technical knowledge and legal industry experience means they always offer us reasoned, pragmatic advice.”
“Trustack always stay one step ahead when it comes to providing the latest products and services. They understand our business and work proactively with our IT team to ensure we always deliver the best service to the firm and our clients.”
Beyond Housing

Maeve Collier
Director of ICT and Change, Beyond Housing
“The technology is there to support us from zero-day onwards in terms of looking at threats and there’s the whole peace of mind that we’ve got knowing we have eyes on our system 24×7.”
“We’ve seen more people talk about training and have a better awareness about it. The education side is effective and simple. You drink a cup of tea, and you watched your video, it’s so quick.”
Leading North-East Energy Business
Head of IT
“We have been working with Trustack for over a decade. We have experienced in-house support, but there are always cases where you need a subject matter knowledge that goes beyond what you can carry internally – Trustack are able to provide in-depth technical expertise and access to vendor support that ensures we can get answers to the most technical of questions. We source our core server, storage, and network products through them, from vendor selection, design, and implementation through to support. This provides a level of assurance and risk mitigation that we will always have a partner available with the technical skills and knowledge of our environment to deal with issues swiftly”.
K Home

Commercial Director
K Home International
“After working with Trustack for over 10 years, we commenced on a long project with Trustack to bring our IT network and infrastructure up to date and hopefully beyond. So far, each stage has been discussed and planned so that we know what to expect and have been given options at each stage to consider so that there are no surprises, and each stage goes to plan. This has meant that any down time has been minimised enabling us to continue operating throughout, all in all very happy with the progress.”