Contact us
Putting your business on the front foot
Get in touch with our committed team for assistance and guidance in navigating the constantly changing technological environment.
Reach out to us today to learn more about our services.

Business hours:
Monday – Friday: 8:30 AM – 5:00 PM
Contact Trustack:
Contact us
Get your business on the front foot
Our dedicated team is available to answer any queries and provide the guidance and support you need to stay secure in today’s ever-evolving technological landscape. Contact us today to learn more about how we can help protect your business.

Where to find us
Cramlington Office (HQ)
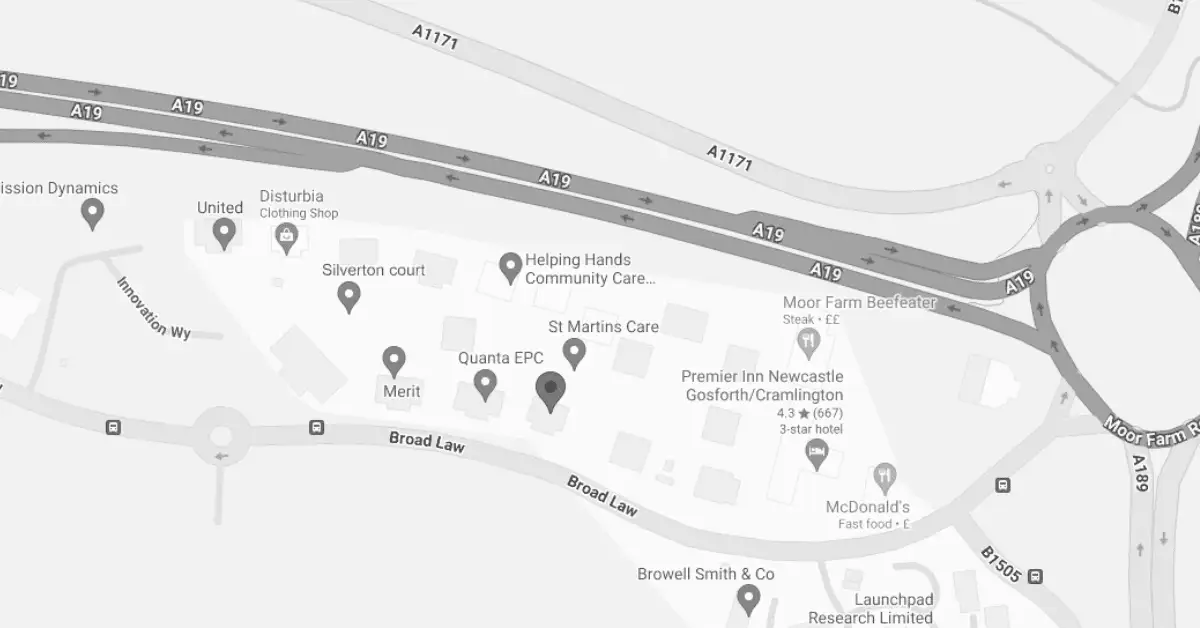
Address:
Cirrus House,
1 Berrymoor Court,
Cramlington,
Northumberland,
NE23 7RZ
Call us:
+44 191 250 3000
Manchester Office
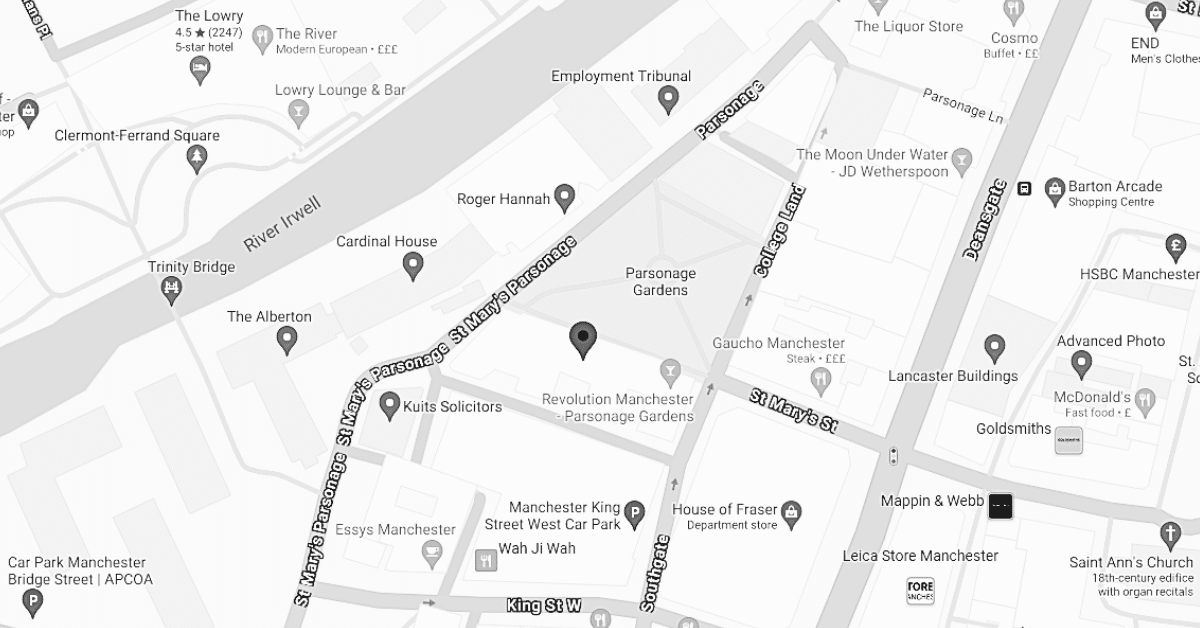
Address:
Arkwright House,
Parsonage Gardens,
Manchester,
M3 2LF
Call us:
+44 191 250 3000
Sunderland Office
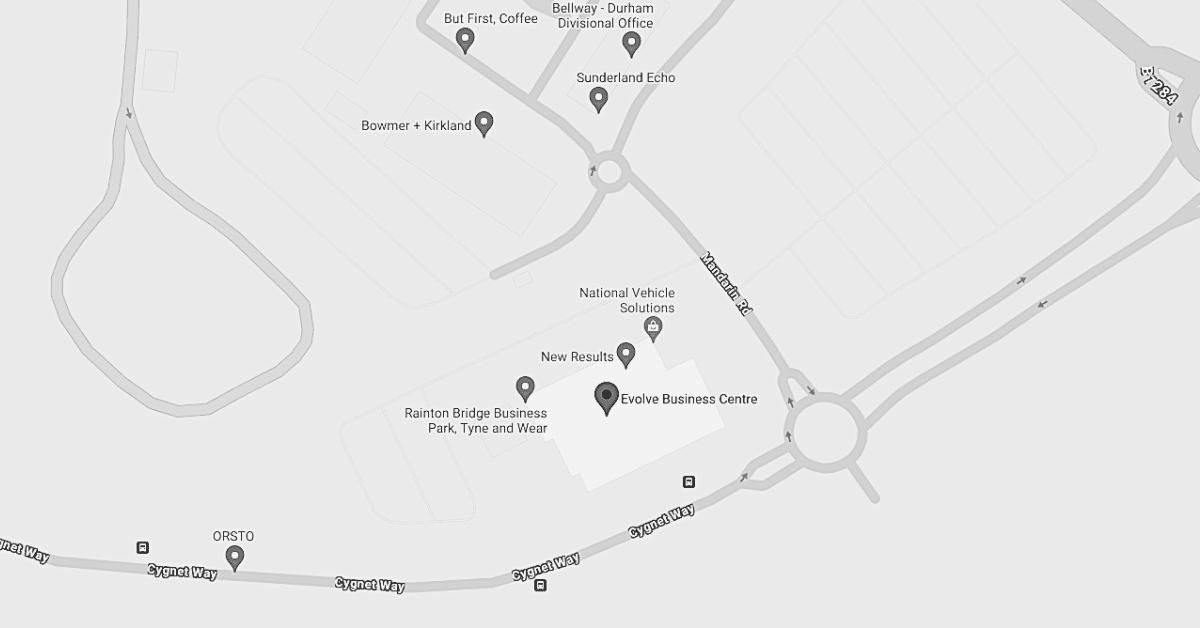
Address:
Evolve Business Centre, Cygnet Way
Rainton Bridge South Business Park,
Houghton-le-Spring,
Tyne and Wear,
DH4 5QY
Call us:
+44 191 250 3000
Why trust our Trustack team?
Expertise:
Our team consists of seasoned cybersecurity professionals with years of experience in the field.
Proven track record:
Trustack has a proven track record of delivering effective cybersecurity solutions to clients across various industries.
24/7 support:
Emergencies don’t wait for business hours, and neither do we. Our dedicated support team is available round-the-clock to assist you.
Tailored solutions:
We understand that every organisation has unique cybersecurity needs. That’s why we offer customised solutions tailored to your specific requirements.
Continuous innovation:
We stay ahead of emerging threats and technologies, ensuring that your defences are always up-to-date and resilient.