Traditional security models are increasingly inadequate. The rise of cloud computing, remote work, and sophisticated cyber threats necessitates a more robust and dynamic approach to cybersecurity. Enter Zero Trust, a security model that fundamentally redefines how organisations protect their data and systems.
Article
Zero Trust is a security framework based on the principle of “never trust, always verify.” Zero Trust is different from traditional security models. Traditional models believe everything inside a network can be trusted.
Zero Trust assumes that threats can come from inside and outside the network. No user or device is trusted by default. This is true whether they are inside or outside the network.

Organisations can enhance the security of their digital assets and maintain the robustness of their networks by strictly following the principles of continuous verification, minimal access privilege, and robust authentication.
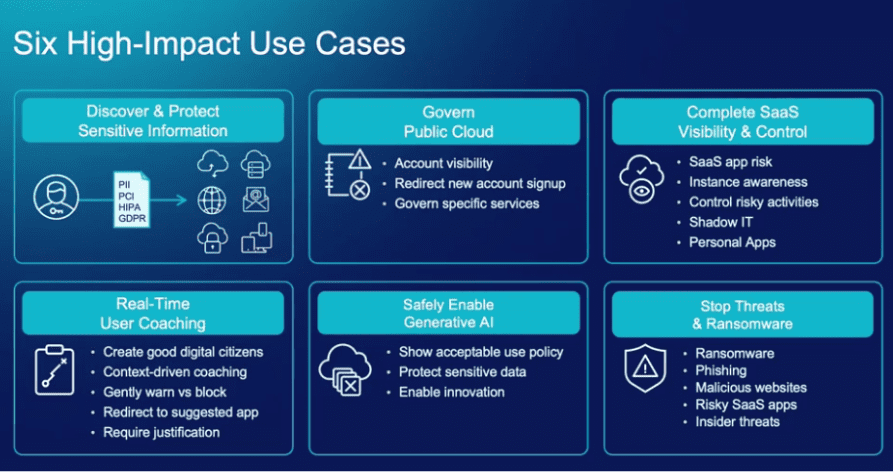
Adopting a Zero Trust model involves several steps:
Regularly Update Security Policies: As cyber threats evolve, so should security policies. Regularly reviewing and updating security protocols keeps the organisation protected against new and emerging threats.
Zero Trust offers enhanced security by continuously verifying users and devices, which significantly reduces the risk of data breaches and unauthorised access. It also improves compliance by helping organisations meet regulatory requirements through strict access controls and robust security measures. Additionally, Zero Trust provides greater visibility into network activities through continuous monitoring, enabling quicker detection and response to potential threats.
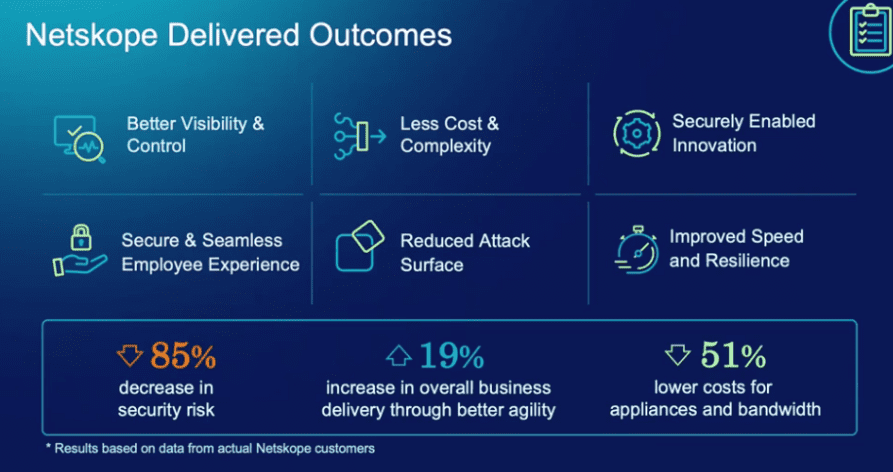
Get your business on the front foot
To provide the best experience on our site, we use technologies like cookies to store and/or access device information. Consenting to these technologies will allow us to process data such as browsing behaviour or unique IDs on this site.